System
intrusion detection
and perimeter violations
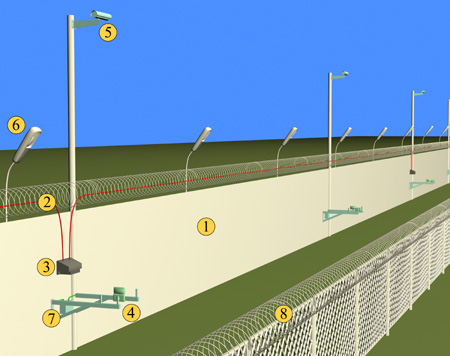
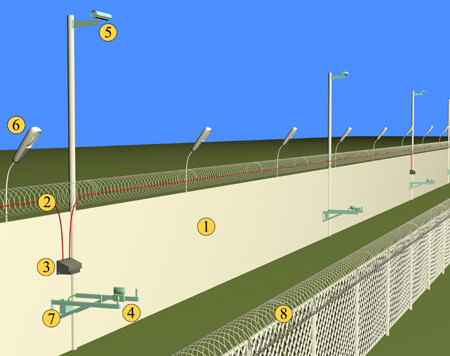
Perimeter security system – a set of hardware and software designed for early detection of attempts to penetrate the protected area.
The main difference between perimeter security systems and other security devices (such as access control and video surveillance) is the detection of intrusion into the territory – and, therefore, taking action – in advance, before the attacker has time to reach the protected object located in perimeter.
The perimeter security system allows:
- identify a possible intruder before he enters the protected area;
- to provide the minimum time of operation of the alarm system from the moment of entrance of the malefactor;
- complicate overcoming the boundaries of protection by the offender;
- perform their functions regardless of external factors – weather, electromagnetic interference, etc.
The perimeter security system can be used at airports, warehouses and industrial enterprises, conventional and nuclear power plants, correctional facilities, petrochemical and refineries, military and defense border lines, and other facilities guarded by a large adjacent territory.
Intrusion detection systems are divided into 4 subspecies:
- Infrared optical systems;
- Cable vibration sensors;
- Radio wave systems;
- Microwave devices.
Infrared optical systems
These devices are one of the most functional perimeter security detectors. Infrared rays, which are constantly sent from transmitter to receiver, are used to detect intrusion. Due to the large distance between the transmitter and receiver, active infrared detectors can reliably protect even large rooms. These systems can be installed off-premises to detect an intruder’s attempt to invade a protected area.
Cable vibration sensors
The principle of operation is based on the registration of mechanical oscillations of the guardrail, which installs a sensitive element that converts these oscillations into an electrical signal, which is processed in the analyzer by a special algorithm, which determines the “alarm” signal.
Both a specialized sensitive cable with microphone properties and point vibration sensors (unaddressed or addressable) can act as a sensitive element.
Radio wave systems
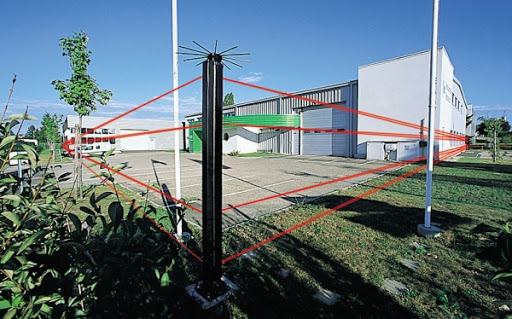
The principle of operation is based on the registration and analysis of the modulation amplitude and shape of the microwave signal at the input of the receiver, which occur when changing the conditions of propagation of radio waves emitted by the transmitter, including when a person moves in the detection zone. The “Alarm” signal is issued when crossing the detection zone by a person or group of people in full height or bent.
Microwave devices
Microwave devices are a three-dimensional perimeter detection system consisting of a digital transmitter and a receiver, which create an invisible microwave safety zone in space between them, when an alarm signal is generated upon intrusion. The combination of microwave detection technology and IR sensors to protect “dead zones” provides the narrowest detection zone among similar systems. This system can be used along fences and fences, pedestrian areas and highways, protecting every meter.